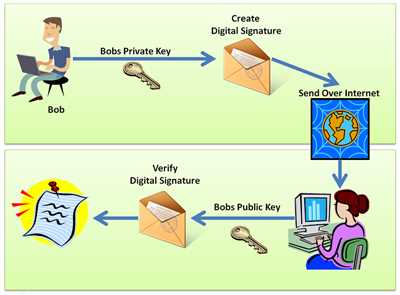
In today’s digitalized world, where most of our important communication happens online, the need for secure and authentic transactions is growing every day. Digital signatures play a vital role in ensuring the integrity and authenticity of digital documents. But how are digital signatures created?
When you sign a physical document, you put your signature on a piece of paper. It’s a unique identifier that belongs to you, and it verifies that you are the one who signed it. In the digital world, it works similarly, but instead of a pen and paper, you use a digital identity.
When you sign a digital document, a process called “digital signing” takes place. It involves using a special function, which converts the data in your document into a hash. This hash is a fixed-sized string of numbers and letters that uniquely represents the content of your document. The hash function ensures that even a small change in the document’s data will result in a completely different hash.
Once the hash is created, it’s combined with your private key using another function, known as the signing function. Your private key is a part of the public-key infrastructure (PKI) and is used for encrypting and decrypting data. The combination of the hash and your private key creates a unique digital signature that can only be generated by you.
Now, let’s say you want to send this signed document to someone. The receiver, who wants to ensure the authenticity and integrity of the document, must perform a few steps:
- Open the document and extract the digital signature.
- Retrieve your public key from a certificate authority (CA), which is a trusted entity that verifies the authenticity of the public keys.
- Use the same hash function on the document to create a new hash.
- Using your public key and the new hash, they can verify if the digital signature matches the document’s content.
If the two hashes match, it means that the document hasn’t been tampered with since you signed it, and the digital signature is considered valid. This process ensures the integrity and authenticity of the document, even when it’s transmitted over an insecure channel like email.
So, what’s the purpose of digital signatures? They provide a way for senders to securely sign their documents and ensure that the recipients can verify the authenticity and integrity of the information they receive. Without digital signatures, it would be challenging to know if the data we receive is from a legitimate source and hasn’t been altered during transit.
In conclusion, digital signatures are an essential part of our digital infrastructure. They allow us to securely send and receive information, knowing that it hasn’t been tampered with and that it comes from a verified source. Understanding how they work can help us stay safe online and ensure the authenticity of our digital transactions.
What do you want to do

In order to understand how digital signatures are created, it is important to first know what they are used for and what their purpose is. Digital signatures are a way to verify the authenticity and integrity of electronic documents or messages. They provide a way to ensure that the data has not been tampered with and that it belongs to the sender it claims to be from.
When you want to sign a document or message using a digital signature, you will need to follow a specific set of steps. First, you will need a digital certificate that contains your own unique identity information. This certificate is issued by a trusted certification authority (CA), such as Signicat or Microsoft, and it acts as a proof of your identity. It includes your public key, which is used for verifying the digital signature.
After obtaining a digital certificate, you can start the process of creating a digital signature. The first step is to take a hash of the document or message you want to sign. A hash is a unique mathematical representation of the data, and it is used to ensure that the document hasn’t been altered in any way. This hash is created using a specific hashing algorithm, such as SHA-256.
Once the hash is created, you will use your private key to encrypt it. Your private key is a secret key that only you have access to, and it is used to create the digital signature. The encryption process ensures that only you, as the signer, can create the signature.
After the digital signature is created, it is attached to the document or message. The receiver can then use your public key, obtained from your digital certificate, to verify the signature. This verification process involves decrypting the signature using the public key and comparing it to the computed hash of the document or message. If the two match, it means that the document or message hasn’t been tampered with and that the signature is valid.
In summary, digital signatures are created using a combination of hashing, encryption, and public key infrastructure (PKI). They provide a way to ensure the authenticity and integrity of electronic documents or messages. Without digital signatures, it would be difficult to verify the identity of the sender and the integrity of the data. Their purpose is to ensure secure and reliable communication between users.
How do digital signatures work
Digital signatures are created using a combination of cryptographic hash functions and public key infrastructure (PKI). They work by allowing a sender to digitally sign a document or message using their own private key, which is unique to them and should be kept secure.
When a sender wants to sign a document, they first create a hash of the document using a hash function. A hash function takes any input and produces a fixed-sized output, which is a unique representation of the original input.
After the hash has been created, the sender encrypts it with their private key, creating a digital signature. The digital signature is then attached to the document or message that they want to send.
On the receiving end, the receiver can use the sender’s public key to decrypt the digital signature and obtain the original hash of the document. If the decrypted hash matches the hash of the received document, it means that the document has not been altered or tampered with during transit.
The receiver can also verify the authenticity of the digital signature by checking the signer’s digital certificate. A digital certificate is issued by a trusted authority, known as a Certification Authority (CA), and contains information about the signer and their public key.
If the digital certificate has been issued by a trusted CA and has not expired, the receiver can trust that the public key used to verify the digital signature belongs to the signer.
By following these steps, digital signatures ensure the integrity and authenticity of documents or messages without the need for physical signatures or in-person verification. They are commonly used in various applications such as email encryption, software updates, and secure online transactions.
How can I get my own digital signature
If you want to get your own digital signature, there are a few steps you need to follow. Here’s what you should do:
- Decide on the purpose: Determine why you need a digital signature. Digital signatures are commonly used to ensure the authenticity and integrity of documents, messages, and data.
- Choose a certification authority (CA): Select a trusted organization that will verify your identity and issue you a digital certificate. The CA will validate that your digital signature belongs to you and ensure the security of the digital infrastructure.
- Create a key pair: Generate a unique pair of cryptographic keys – one private and one public. Your private key should be kept secret, while the public key will be widely available.
- Apply for a digital certificate: Submit your public key, along with the necessary identification information, to the chosen CA. They will use this information to create a digital certificate for you.
- Store your private key securely: Since your private key is integral to the security of your digital signature, it should be stored in a safe and tamper-proof location. A hardware token or secure software solution can be used for this purpose.
- Install the certificate: Once you have received your digital certificate, you should install it on your computer or device. This will enable you to use your digital signature when signing documents, emails, or other forms of electronic communication.
Following these steps will allow you to have your own digital signature, which you can then use to sign and verify the authenticity of your digitally signed documents and messages. Remember, digital signatures provide assurance that the data has not been tampered with and ensure the integrity of your communication without the need for in-person verification.
Digital signature FAQs
What is a digital signature?
A digital signature is a cryptographic function used to verify the authenticity and integrity of a digital document or message. It is created using a signing algorithm that uses a private key to encrypt a hash of the document or message. The resulting encrypted data, known as the digital signature, can be decrypted using the corresponding public key to verify its authenticity.
How does a digital signature work?
When a sender wants to digitally sign a document or message, they first create a hash of the data using a hash function. They then encrypt this hash using their private key to create the digital signature. The signed document, along with the digital signature, is then sent to the receiver.
The receiver, using the sender’s public key, can decrypt the digital signature to obtain the hash value. They can then create their own hash of the received document or message and compare it with the decrypted hash. If they match, it means the data has not been tampered with and the signature is valid.
What is the purpose of a digital signature?
The purpose of a digital signature is to verify the authenticity and integrity of a digital document or message. It ensures that the data has not been altered or tampered with during transit and provides assurance that the sender is who they claim to be.
How are digital signatures different from digital certificates?
Digital signatures are created using cryptographic functions and are used to verify the authenticity and integrity of data. Digital certificates, on the other hand, are issued by a Certificate Authority (CA) and are used to verify the authenticity of individuals or organizations.
A digital certificate contains information about the certificate holder, such as their name and public key, and is used to verify the identity of the signer. It is used in conjunction with digital signatures to provide a higher level of trust and security.
What’s the role of a Certificate Authority (CA) in digital signatures?
A Certificate Authority (CA) is a trusted third-party organization that is responsible for issuing digital certificates. The CA verifies the identity of individuals or organizations and signs their digital certificates using its own private key.
The CA’s public key is widely distributed and trusted, allowing users to verify the authenticity of the digital certificates issued by the CA. This establishes trust in the identity of the certificate holder and ensures the integrity of the digital signatures generated using the certificates.
Do I need my own digital certificate to use digital signatures?
Yes, to use digital signatures, you will need your own digital certificate. The digital certificate contains your public key, which is used to verify the authenticity of your digital signatures. The private key, which corresponds to your public key, is used to create the digital signatures.
You can obtain a digital certificate from a trusted Certificate Authority (CA) by following their specific procedures and requirements. Once you have your digital certificate, you can use it to sign documents and messages, providing assurance of their authenticity.
What format are digital signatures stored in?
Digital signatures are typically stored in a binary format, such as PKCS#7 or XML signature format. These formats contain the encrypted data that represents the digital signature, along with any necessary metadata or additional information.
The specific format used for storing digital signatures may vary depending on the software or platform being used. It is important to ensure compatibility between different systems when working with digital signatures.
How can I verify a digital signature?
To verify a digital signature, you will need the signed document or message, the digital signature itself, and the corresponding public key of the signer. The verification process involves decrypting the digital signature using the public key to obtain the hash value. A hash of the document or message is then created, and the two hash values are compared. If they match, the signature is valid and the data has not been tampered with.
Most software applications that support digital signatures will have built-in verification functions that automate this process, making it easy to verify the authenticity of digitally signed documents or messages.
Is digitally signing the same as encrypting

Digital signing and encrypting are two distinct processes when it comes to data security. While both are used to ensure the authenticity and integrity of information, they serve different functions and use different methods.
Digital signing involves the use of a digital signature, which is a cryptographic mechanism that verifies the identity of the signer. When signing a document or message, the signer creates a unique digital signature using their private key. This signature is then attached to the document or message, creating a tamper-evident seal that can be used to verify the integrity and authenticity of the data.
On the other hand, encrypting involves using a cryptographic algorithm to scramble the content of a document or message, making it unreadable to unauthorized individuals. The encrypted data can only be decrypted and accessed using a matching decryption key.
So, while signing ensures the authenticity and integrity of data, encrypting is focused on protecting the confidentiality of the data.
In terms of the tools and processes used, digital signing often relies on a Public Key Infrastructure (PKI) and a Certificate Authority (CA). The signer’s private key is used to create a hash of the data, which is encrypted using the private key. The encrypted hash, along with the signer’s public key and other relevant information, is then packaged into a digital signature format. This signature can be verified using the signer’s public key and the original data.
Encrypting, on the other hand, uses symmetric or asymmetric encryption algorithms, where a shared or public key is used to encrypt the data, and a matching private key is used to decrypt it.
In summary, while both digital signing and encrypting are essential for data security, they have different purposes and mechanisms. Signing ensures the integrity and authenticity of data, while encrypting protects the confidentiality of data.
What’s a hash function
A hash function is a fundamental component of the cryptographic infrastructure used to create digital signatures. It is a mathematical algorithm that takes an input (such as a document or data) and outputs a fixed-size string of characters, called a hash value or hash code. The hash function creates a unique fingerprint for the input, which is used to ensure the authenticity and integrity of the information.
Hash functions are widely used in many areas of digital security and are essential for digital signatures. When a digital signature is created, the hash function is applied to the document or data that is being signed. The resulting hash value is then encrypted with the signer’s private key. The encrypted hash value, along with the signer’s public key, is included in the digital signature.
When the receiver of the signed document or data wants to verify its authenticity, they can use the same hash function to create a hash value from the received document or data. They can then decrypt the encrypted hash value in the digital signature using the signer’s public key. If the decrypted hash value matches the hash value generated from the received document or data, the signature is considered valid and the document has not been tampered with.
Hash functions have several important characteristics that make them suitable for digital signature purposes. First, they are one-way functions, which means that it is computationally infeasible to determine the original input from the hash value. Second, they have a fixed output size, regardless of the size of the input data. This allows for efficient storage and comparison of hash values.
Popular hash functions used for digital signatures include SHA-256 (Secure Hash Algorithm 256-bit) and MD5 (Message Digest Algorithm 5). It is important to use a well-known and widely accepted hash function to ensure the security and integrity of digital signatures.
What’s a digital certificate
A digital certificate is a cryptographic document that verifies the authenticity of a digital signature. It is issued by a certification authority (CA) and contains key information about the signer’s identity, public key, and the purpose for which the certificate can be used.
When you want to send encrypted or digitally signed emails, documents, or data, you can use a digital certificate to verify the identity of the sender and ensure that the content hasn’t been tampered with or altered. The digital certificate is signed by the certification authority, creating a chain of trust in the digital certificate infrastructure.
The digital certificate also functions as an electronic “passport” for the signer, allowing them to prove their identity in an online environment. It enables users to securely transmit and receive information and validate the authenticity of signed documents.
So how does a digital certificate work? When a signer wants to digitally sign a document or data, they use their own private key to create a unique hash, or fingerprint, of the document. This hash is then encrypted with the signer’s private key, creating a digital signature that is unique to the document and the signer.
When someone wants to verify the digital signature, they use the signer’s public key to decrypt the signature. If the decrypted signature matches the hash of the document, then the signature is valid and the document has not been altered since it was signed.
A digital certificate is stored in a specific format and usually comes in a pair: a public key certificate, which belongs to the signer, and a private key, which is securely stored and used by the signer to create digital signatures. The public key is freely available to anyone who wants to verify the signature.
There are different types of digital certificates, each with its own purpose. Some certificates are used for email encryption, while others are used for signing documents or authenticating the identity of users in an online system.
| FAQs | Answers |
|---|---|
| What is PKI? | PKI stands for Public Key Infrastructure, which is the framework that enables the secure exchange of information using digital certificates. |
| What’s the function of a Certification Authority (CA)? | A Certification Authority (CA) is a trusted third-party organization that issues and verifies digital certificates. |
| What’s the purpose of using digital signatures? | Digital signatures are used to ensure the authenticity, integrity, and non-repudiation of electronic documents and data. |
In summary, a digital certificate is a crucial component of the digital signature infrastructure. It provides a means to verify the authenticity of signatures and ensure that the content hasn’t been tampered with. Digital certificates are widely used to secure and authenticate electronic communications and documents.
What’s a certificate authority CA
A certificate authority (CA) is a trusted entity that issues digital certificates, which are used to verify the authenticity and integrity of digital signatures. In the context of digital signatures, a CA provides a central infrastructure that ensures the security and trustworthiness of the signed documents.
When you want to digitally sign a document, you can follow the following steps:
- The signer creates a hash, or a unique representation of the document using a specific algorithm.
- The signer encrypts the hash with their private key to create a digital signature.
- The signer sends the signed document along with the digital signature to the receiver.
- The receiver can then use the signer’s public key, which belongs to the same CA, to verify the integrity and authenticity of the document.
A certificate authority plays a crucial role in this process as it acts as a trusted third party that verifies and certifies the signer’s identity. By issuing digital certificates, the CA ensures that the public key used for verifying signatures actually belongs to the signer.
The CA’s digital certificate contains information about the signer, the CA itself, and the validity period of the certificate. It is signed by the CA using its private key, and can be used by anyone to verify the authenticity of the digital signatures.
Without a certificate authority, the process of verifying digital signatures would be more challenging and prone to fraud. A CA provides a trusted infrastructure for verifying the authenticity of signed documents, ensuring that they have not been tampered with or altered.
So, if you ever receive a digitally signed document and want to verify its authenticity, you can check the digital signature using the signer’s digital certificate provided by the CA. This allows you to trust the document and the information it contains.
Now that you know what’s a certificate authority, let’s see some frequently asked questions (FAQs) about this topic:
| FAQ | Answer |
| How does a CA work? | A CA works by verifying the identity of individuals or organizations and issuing digital certificates to them. These certificates are used to digitally sign documents and verify their authenticity. |
| What’s the purpose of a CA? | The purpose of a CA is to ensure the security and trustworthiness of digital signatures by verifying the identity of signers and issuing digital certificates that can be used to verify their signatures. |
| What should I do if a digital signature hasn’t been verified? | If a digital signature hasn’t been verified, it means that the document may have been tampered with or the signer’s identity hasn’t been properly verified. In such cases, you should contact the signer or the CA for further verification. |
In conclusion, a certificate authority (CA) is an essential part of the public key infrastructure (PKI) that is used in digital signatures. It ensures the authenticity and integrity of documents by verifying signers’ identities and issuing digital certificates. Without a CA, the process of digitally signing and verifying documents would be less secure and trustworthy.
What’s public key infrastructure PKI
Public Key Infrastructure (PKI) is a system that is used to manage digital certificates and enable the secure exchange of information over electronic networks. It provides the necessary framework for creating and managing digital signatures, as well as ensuring the authenticity and integrity of digital documents.
PKI involves a combination of software, hardware, policies, and procedures to establish a secure and trusted environment. It relies on the use of asymmetric encryption algorithms, where each user has a pair of cryptographic keys – a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt it.
The main purpose of PKI is to verify the authenticity of digital documents and the identity of the signers. When a sender wants to sign a document with a digital signature, they should use their private key to apply a mathematical function to the document’s hash value, creating a digital signature. This signature is unique to the document and cannot be altered without invalidating the signature.
To ensure the authenticity of the digital signature, the recipient can use the sender’s public key to verify the signature. If the signature is valid and the document has not been tampered with, it can be trusted. This process provides a way for senders and receivers to securely exchange messages and documents over open networks.
PKI relies on a chain of trust called a certificate hierarchy. There are different types of certificates involved in PKI, including root certificates, intermediate certificates, and end-user certificates. Root certificates belong to trusted certificate authorities (CAs) and serve as the foundation of the PKI infrastructure. Intermediate certificates are used to bridge the gap between the root certificates and the end-user certificates.
When you receive a digitally signed document, the authenticity of the signature can be verified by checking the certificate used to sign it. The certificate contains information about the signer and is issued by a trusted CA. By verifying the certificate chain and checking the validity of the signer’s certificate, you can ensure the authenticity and integrity of the signed document.
PKI is widely used in various applications, such as secure email communication, digital signatures for online transactions, and secure access to online services. It plays a crucial role in ensuring the confidentiality, integrity, and authenticity of digital information in today’s digital world.
Sources
There are several sources involved in the creation of digital signatures:
| Source | Description |
|---|---|
| Senders | Users who send digitally signed documents or messages. |
| Certificates | Electronic documents that verify the identity of the signer and are used to sign the data. |
| Certificate Authority (CA) | An organization that issues certificates and ensures the authenticity of the signer’s identity. |
| Public Key Infrastructure (PKI) | The infrastructure used to manage certificates, public and private key pairs, and verify the integrity of the signed documents. |
When a sender wants to digitally sign a document, they first need to obtain a certificate from a trusted CA. This certificate ensures that their identity belongs to them and can be used for signing purposes. The sender then uses their private key to sign the document, which creates a digital signature in the form of a hash. This signature can be used to verify the authenticity and integrity of the document.
To verify a digital signature, the recipient of the document can use the sender’s public key, which is stored in their certificate. The recipient can then check the signature against the document to ensure it hasn’t been tampered with. The CA’s certificate is also used to verify the authenticity of the sender’s certificate.
Without proper sources and verification, digital signatures may not be trusted, and the integrity of the signed documents may be compromised.